Table of Contents
ToggleUnderstanding the SEC’s 4-Day Breach Disclosure Rule
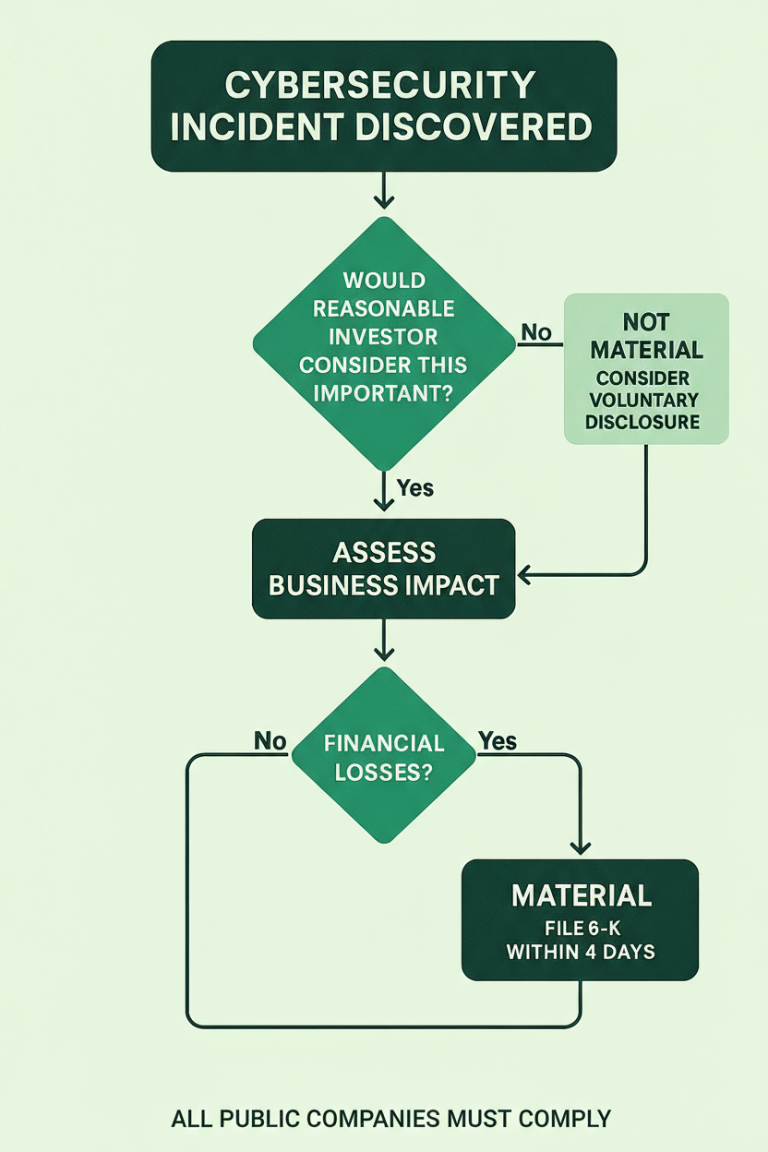
In July 2023, the U.S. Securities and Exchange Commission (SEC) adopted new cybersecurity disclosure rules that put public companies on a strict timeline. When a company determines that a cyber incident is “material,” it must disclose the incident via a Form 8-K within four business days of that determination[1]. The disclosure (a new Item 1.05 on Form 8-K) must describe the incident’s nature, scope, timing, and its material or likely material impact on the business[2]. Importantly, the SEC expects management to make the materiality call without “unreasonable delay” after discovering an incident[3] – you can’t wait around hoping an incident blows over. If a reasonable investor would consider the incident important, it’s likely material by SEC standards.

What not to include: The SEC does not want companies spilling sensitive technical details in these public reports if it would hinder incident response or remediation. In fact, Instruction 4 of Item 1.05 explicitly allows companies to omit specific technical information – like details of their response plans or system vulnerabilities – that could aid attackers or impede the fix[4]. The focus of the disclosure should be on the business impact, not a play-by-play for hackers.
Timing nuances: The four-business-day clock starts once you decide the incident is material – not when you first discover the event[1]. If you’re still investigating and haven’t determined materiality, the countdown hasn’t begun, but you are expected to decide as soon as reasonably possible[3]. Companies sometimes choose to voluntarily disclose a significant incident even before making a materiality determination (to keep stakeholders informed). The SEC has advised doing such early disclosures under Item 8.01 (Other Events), which is a catch-all section, not under Item 1.05[5]. If you later conclude the incident is material, you then must file a Form 8-K under Item 1.05 within four business days of that decision, even if you already gave an initial update under Item 8.01[6]. (The Item 1.05 filing can reference your earlier report but still needs to include all required details of the incident[6].)
Scope of the rule: This 4-day breach disclosure requirement now applies to essentially all U.S. public companies as of early 2024. Larger companies had to start complying by late 2023; smaller reporting companies got an extra 180 days (until around June 2024) to begin reporting[7]. Foreign private issuers have parallel requirements (material incidents get reported in Form 6-K, and annual cyber risk disclosures in Form 20-F)[8]. In short, no listed company is exempt from prompt breach reporting.
Exceptional delays: What if disclosing the hack publicly within 4 days would itself pose a grave risk (for example, to national security)? The rule provides a narrow out: if the U.S. Attorney General deems that immediate disclosure would threaten national security or public safety, the company can get a delay of up to 30 days[9]. This delay can potentially be extended by another 30 days (and in extraordinary cases, a final 60 days) with further Attorney General determinations[10][11]. However, treat this as a rare exception, not the rule. Even if a delay is requested, you should continue preparing the disclosure on schedule – the 4-day clock doesn’t stop ticking unless an official delay is actually granted. Barring a clear national security issue (which most breaches won’t meet), assume you’ll be filing on time.
Finally, note that making the initial 8-K filing is not the end of the story. If new material facts emerge later, or if some required details weren’t confirmed by the filing date, you’re obligated to amend your Form 8-K within four business days of determining that information[12]. In practice, that means file what you know by the deadline, even if some aspects are still under investigation, and plan for a follow-up disclosure[13] once you have more clarity.
The M&A Challenge: Breaches Timing vs. Deal Timing
Complying with the 4-day breach rule is hard enough in normal times, but it can be especially chaotic if you’re in the middle of a merger or acquisition. M&A transactions are exactly when both cybersecurity risks and disclosure obligations can collide in complex ways. Here’s why M&A situations complicate the 96-hour breach timeline:
- No “deal exception” to the rule: If a cybersecurity incident occurs in a third-party system – say, in a target company’s network during acquisition due diligence, or a critical vendor’s system – you don’t get extra time just because it wasn’t your own system. The materiality test looks at impact to the registrant (the public company), regardless of where the breach occurred. So if the incident
materially affects the acquirer’s business or the deal, the acquirer (as the registrant) faces the 4-day disclosure clock once it determines the impact is material. In other words, a breach at a target or partner can quickly become your problem to disclose to investors if it alters the risk profile or economics of the deal.
- Deal terms at stake: In an M&A contract, a cyber incident can trigger or affect representations & warranties, purchase price adjustments, indemnification clauses, or even give a party grounds to walk away under a Material Adverse Change (MAC) clause[14][15]. That means a significant breach discovered during deal negotiations or due diligence isn’t just an IT issue – it’s a legal and valuation issue. Buyers and sellers should proactively address this by including robust cybersecurity representations, warranties, and covenants in the agreement, and by defining clear remedies or price adjustments if an incident comes to light. If you’ve negotiated these terms before signing, you’ll be in a much better position to respond within four days because everyone knows the rules of engagement (for example, what must be disclosed, who bears certain costs, etc.).
- Need for controlled communications: A public breach disclosure in the middle of an acquisition could roil the deal – impacting investor sentiment, employee morale, and customer trust – unless it’s handled carefully. At the same time, you must keep key stakeholders like potential acquirers, merger partners, lenders, customers, and regulators in the loop about what’s going on. The SEC’s rule doesn’t prohibit private communications with these parties, as long as you’re not engaging in improper selective disclosure. The practical approach is to brief critical counterparties in a controlled, confidential manner. For example, if you’re in a live deal process, you might update each bidder or your lending bank about the situation inside a secure data room, rather than via casual emails. Use NDA protections and secure Q&A forums to field their questions. By containing these discussions within a virtual data room (VDR) or other auditable channel, you ensure that what you share is tracked, time-stamped, and only accessible to intended recipients. This keeps rumors at bay and proves you weren’t giving anyone an unfair informational advantage – you were simply managing the flow of necessary information under confidentiality. It also helps later on to show regulators or courts that you handled the communications responsibly.
In short, during M&A you have to juggle deal negotiations and breach response simultaneously. The key is tight process control: address cyber risks in the contract early, move fast on the materiality decision, and communicate need-to-know information through secure, logged channels. Now, let’s break down how to actually execute all of this in the crucial 96 hours after a material incident hits.
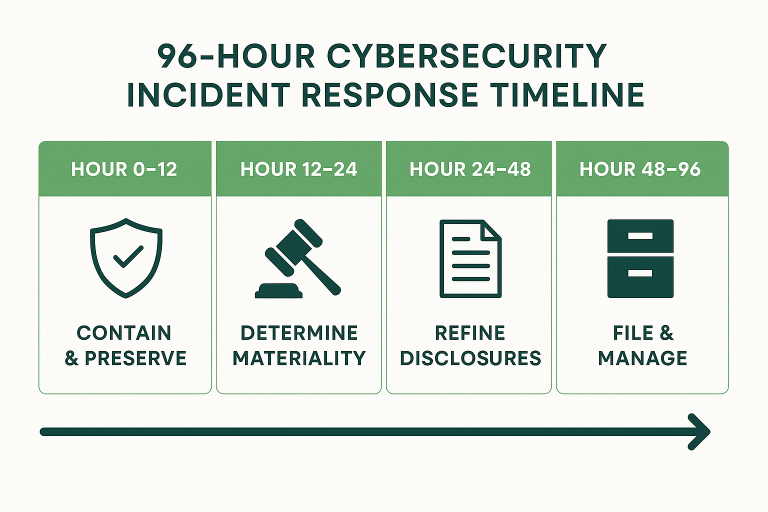
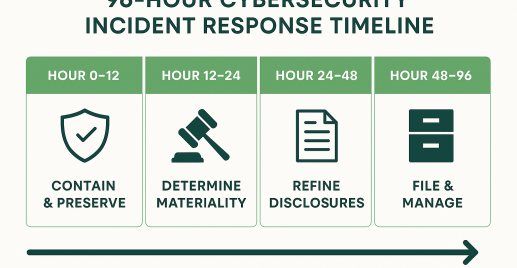
The 96-Hour Incident Response Playbook (Phase by Phase)
When a serious cybersecurity incident strikes, the clock starts ticking the moment you decide it’s material. You’ve got four business days to investigate, manage the fallout, draft accurate disclosures, and file with the SEC. That’s effectively 96 hours (plus any intervening weekend hours) to get everything done – a sprint, not a stroll. The only way to survive this sprint is to have a disciplined playbook that your team can follow step by step. Below is a four-phase breach response playbook designed for speed and control, especially suited for scenarios like M&A due diligence where multiple parties are involved and information must be handled delicately. Each phase covers roughly 12–24 hours of the timeline:
Hour 0–12: Contain, Preserve, and Cordon Off
- Stand up a “war room” in a secure data repository: Immediately set up a confidential incident war room, ideally in a virtual data room (VDR) or similar secure collaboration space. Create dedicated folders for key workstreams – for example: Incident Timeline, Materiality Analysis, Draft 8-K Disclosure, Board Updates, Customer Notifications, Vendor Impact, etc. Lock down access so that only the core incident response team (legal, security, executives, and essential advisors) is allowed in. Enable detailed activity tracking and audit logs from the start. Every document view, edit, download, or Q&A exchange should be recorded and attributable to a specific user. This creates an evidence trail showing exactly who did what and when – critical for proving later that you acted swiftly and responsibly.
- Preserve evidence and map the scope: In these first hours, the cybersecurity team’s priority is to contain the incident and gather forensic evidence, while the legal team’s priority is to assess potential impact (materiality). These efforts happen in parallel. Have your IT forensics leads capture key technical indicators (system logs, malware samples, affected asset lists) and isolate affected systems to prevent further damage. Simultaneously, have your legal/compliance team begin filling out a “materiality worksheet” in the war room. This worksheet is essentially a running list of what the incident could mean for the business: e.g. which operations are disrupted, preliminary estimates of financial loss or costs, any sensitive data compromised (and regulatory implications of that), potential impact on customers or vendors, contractual breaches (like SLAs or M&A clauses triggered), reputational damage, etc. Don’t worry about exact figures yet – the goal is to quickly form a defensible view of whether this incident is material, not to complete a full post-mortem. The SEC expects you to make the materiality determination promptly, not wait for a perfect analysis[3]. Documenting your reasoning as you go helps show that the determination was made in good faith based on what was known at the time.
- Lock down document handling and access: From the get-go, implement strict controls on any documents or information related to the incident. This prevents well-intentioned team members or external partners from inadvertently leaking news of the breach before you’re ready. Apply dynamic watermarking on all documents exported from the data room – i.e. every page that someone downloads is stamped with that person’s email or name, IP address, and a timestamp. That discourages anyone from circulating screenshots or printouts. Require single sign-on (SSO) and limit access by IP range if possible, so only authorized users on known networks can even reach the war room. And critically, enable digital rights management (DRM) on sensitive files. DRM allows you to revoke access or delete files remotely even after someone has downloaded them. For example, if a confidential draft of the 8-K or a legal memo somehow gets sent outside the approved circle, you can kill its access before it spreads. These measures keep the incident response tightly cordoned off from the rest of the organization (and the world), buying you precious time to control the narrative.
Hour 12–24: Determine Materiality & Start the Disclosure Clock
- Hold the “materiality huddle” and make the call: By roughly half a day in, you should have enough preliminary info to convene top decision-makers for a materiality assessment. This usually means the General Counsel (or chief legal officer), Chief Information Security Officer (CISO), Chief Financial Officer, head of Investor Relations, and outside breach counsel, among others – essentially, the group responsible for SEC disclosures and cybersecurity. Review the materiality worksheet and ask the key question: “Would a reasonable investor consider this information important?” If the consensus is Yes – this incident is material – then the 4-day SEC filing clock officially starts now[1]. Mark this decision time in your records. Immediately task someone to kick off a Form 8-K draft (Item 1.05 disclosure) covering what happened. The drafting should focus on the known facts about the nature of the incident, its scope and timing, and the impact or likely impact on the company’s finances or operations[2]. Don’t wait for every detail – if you know enough to call it material, you know enough to start writing the disclosure. At the same time, if any urgent containment or remediation steps** are still in progress, ensure those continue (containment can’t stop just because you’re drafting a disclosure).
- If you’re not yet sure it’s material: It’s possible the team concludes at 12 hours in, “We think this might not be material, or we need more data to be sure.” That’s okay – the obligation is to decide “without unreasonable delay,” not necessarily within 12 hours, if the facts aren’t all in[3]. However, do not use uncertainty as an excuse to drag feet. Continue investigating aggressively, update the impact analysis, and aim to make the materiality determination as soon as possible (e.g. in the next day or two). If the incident is leaning toward non-material but still significant, you have the option to proactively disclose it under Item 8.01 (voluntary disclosure) before the 4-day clock ever starts[5]. Some companies choose this route to be transparent with investors early on. Remember, though, if the situation later evolves to material, you’ll need to follow up with the official Item 1.05 8-K filing within four days of that materiality decision[6]. In short: keep reassessing as new information comes in, and document why you believe it is or isn’t material at each stage.
- Quietly update key stakeholders under NDA: Concurrently with drafting your public disclosure (or continued analysis), begin selective, confidential briefings to those who need to know. This can include your cloud providers or security vendors (for incident response help), major customers expecting updates per contracts, your board of directors, insurers, and – in an M&A context – any merger partners, bidders, or lenders involved. The SEC’s 4-day rule does not bar companies from conducting normal incident response communications; it simply mandates when you must tell the market. So coordinate private notifications as needed, but do it carefully. The safest approach is to use the secure data room or a similar encrypted communication channel for these disclosures. For example, you might post a confidential memo in a dedicated folder for “Customer Notifications” in the VDR, or use a built-in Q&A module to let, say, a potential acquirer submit questions and receive answers about the incident within the platform. This keeps all sensitive Q&A logged and prevents information from leaking via forwarded emails or side conversations. Make sure each audience only has access to the materials intended for them (e.g. the bidder doesn’t see the customer notice, and vice versa). By hour 24, your goal is that the right people outside the core team have been briefed, under confidentiality, and all such communications are documented. This ensures no one important is blindsided by the eventual public 8-K, and it reduces the risk of rumors – yet you haven’t tipped off the broader market prematurely.
Hour 24–48: Refine Disclosures and Prepare Broader Communications
- Draft the Form 8-K like a surgical report: With perhaps 2–3 days left on the SEC clock, focus on producing a clear, accurate disclosure for the 8-K filing. Write and refine it inside your secure war room so that every edit is captured. The 8-K Item 1.05 statement should read like a high-level incident summary for business readers, not a technical post-mortem. Stick to what investors need to know: What happened? When did we discover it? What systems or data are impacted? How is it affecting (or likely to affect) our business or financials? Avoid speculative or overly detailed statements – if certain facts are still unknown, it’s fine to say so (and you’ll update later)[12]. At the same time, don’t sugarcoat or hide material impact. If operations are disrupted or losses have occurred, say that in appropriate general terms. Leave out the “breadcrumbs” that would help attackers[4]. For instance, you might disclose that “a network intrusion affecting our customer billing system was detected on March 1,” but you do not need to publish the specific vulnerability exploited or the exact malware used (especially if the incident is ongoing). The SEC explicitly allows withholding technical details that would impede response[4]. Have legal counsel review the draft closely to ensure it meets the requirements without over-sharing. By the end of this phase, you should have a near-final 8-K draft ready for executive sign-off and any board review required before filing.
- Stage all documents and exhibits in one place: If your disclosure will include any attachments or exhibits (say, an update that will also be shared as a press release or a customer notification letter), keep those within the secure data room for review. Use the platform’s features to distribute drafts to reviewers with need-to-know access only. For instance, you might give the CFO and CEO view-only access to the Draft 8-K folder for approval purposes, with dynamic watermarking on any download. If they pull down a PDF to read, it’s stamped with their name so they won’t circulate it further. As a further precaution, enable “expire after download” or file expiration if your VDR supports it (e.g., CapLinked’s FileProtect feature) – this means that even the approved reviewers will lose access to the file after a short time, reducing the window in which a stray copy could leak out. Essentially, you are treating the disclosure documents themselves as highly sensitive until the moment of public filing.
- Draft tailored notices for customers, partners, and others: Alongside the SEC filing, you may need to inform other stakeholders (clients, vendors, employees, etc.) about the incident, especially if their data is involved or their operations are affected. Use the 24–48 hour window to prepare these communications in advance. Craft messaging that aligns with the 8-K but is tailored to the audience (for example, a customer breach notification might include support contact info or remediation steps, which wouldn’t be in the 8-K). Again, keep these drafts in the secure war room. Utilize group-specific permissions so that once ready, you can share the customer notice only with the customer relations team, the vendor notice only with procurement/legal, and so forth. This compartmentalization ensures that if any one notice leaks, it’s easier to trace, and other stakeholders don’t see communications not meant for them. Also plan the method of delivery – many companies use the data room or an encrypted email service to send out such notices at the appropriate time (usually right after the public 8-K goes live).
- Coordinate press or PR strategy (if applicable): If the breach is likely to draw media attention, your communications or PR team should be looped in to draft a public statement or press release consistent with the 8-K. Often the Form 8-K filing itself will double as the company’s public statement, but be prepared for inbound questions. Decide in this phase who will serve as the company’s spokesperson and arm them with a Q&A or talking points drawn from the 8-K content. (All of this can be documented in the data room too.)
- Consider the Attorney General delay – but don’t count on it: As mentioned, if there’s a plausible case that immediate disclosure poses a national security or public safety risk (for instance, involvement of law enforcement or critical infrastructure concerns), your counsel might be seeking an Attorney General delay. If you are pursuing this, the legal team should have already notified the SEC as required and be in active talks with the authorities. However, do not slow down your preparation waiting on an answer. Unless you get a definitive written determination from the Attorney General before the 8-K deadline, you must be ready to file. Treat an approved delay as a contingency – a bonus 30 days at most – not as the plan. If by hour 48 you have indication a delay will be granted, you might adjust the final disclosure timing, but keep everything primed. Conversely, if a delay is granted or later lifted, maintain all interim draft materials and communications inside the secure data room. Continue to control access and log all updates during the extended period. When the delay expires or is revoked, you should be in a position to file the 8-K immediately. The overarching principle is: Only a formal blessing from the Attorney General stops the clock – lacking that, assume you’re on the original schedule.
Hour 48–96: File, Disclose, and Manage the Fallout
- Meet the deadline: file the 8-K on time. By the fourth business day’s due date, ensure the Form 8-K is filed with the SEC’s EDGAR system, containing all required information about the incident[1][2]. Remember, the countdown was based on when you made the materiality determination, not when the incident happened. For example, if an incident was discovered on January 1 and you deemed it material on January 5, the four business day window starts January 5. Don’t miss this deadline – late filing can expose the company to SEC enforcement or shareholder lawsuits. If you are racing the clock, it is better to file an incomplete report on time than a perfect report late. The SEC allows that if certain details are not yet available, you can say so in the 8-K and then file an amendment later once those details are determined[12]. Regulators expect that you amend promptly (within four business days) when new material info comes to light[12]. The key is to demonstrate that you disclosed everything material that was known by the deadline, and you didn’t sit on anything important.
- Control the narrative with stakeholders: Once the 8-K is public, you enter the phase of damage control and follow-up. Leverage your secure data room to continue managing communications in a controlled way. For instance, if you had bidders or partners in the loop via the VDR Q&A, post a copy of the filed 8-K in a dedicated folder or send it through the Q&A to those parties immediately so they have the official info. Host any further Q&A about the incident through that same channel – this keeps a single source of truth and an audit trail of who asked what and what was answered, which is invaluable if there are later disputes. It’s far better to answer a lender’s detailed question inside a logged Q&A module than over an email or phone call that leaves no record. Internally, coordinate with your investor relations team to address any investor or analyst inquiries with the consistent facts from the 8-K. If a public press release or customer notification is being issued around the same time, ensure those messages don’t contradict the 8-K (they should echo its content, just tailored in tone).
- Tighten data room security post-disclosure: In the first day or two after the breach disclosure, your incident response is still ongoing and sensitive analysis documents may still be in the war room. Monitor the data room’s activity logs for any unusual access patterns – e.g. someone trying to download large volumes of files or a user accessing sections they never did before. It’s possible that once the news is out, more people (with access) get curious and poke around the documents. If you detect any concerning behavior or if certain materials have served their purpose, dial back permissions accordingly. For example, you might remove outside counsel’s junior analysts from access once drafting is done, or revoke download ability for a particularly sensitive forensic report now that the 8-K is filed. Use the DRM capabilities to pull back any documents that are no longer needed outside the core team – you don’t want detailed post-incident analysis floating around if it’s not necessary.
- Revoke or secure any privileged analysis: Often during a breach, the company’s law firm will prepare a privileged report on what happened and how to prevent it going forward. Such a report (and similar communications) should remain highly restricted to preserve attorney-client privilege. After the disclosure, decide what to do with these documents – many firms will keep them only on their systems, but if they were in your data room, consider moving them to an attorney-only folder with strict DRM or deleting the copies, with the master remaining with counsel. The principle is to limit the spread of sensitive investigative information that adversaries (or plaintiffs’ lawyers) would love to get hold of.
- Plan the follow-ups and long-term fixes: Just because the 8-K is filed doesn’t mean the work is over. In the days and weeks after, you should be preparing any required follow-up disclosures. For instance, if some material facts were not confirmed by the initial filing, when they do firm up you’ll need to file an amended 8-K Item 1.05 within four business days of that discovery[12]. Also, the SEC’s rules now require that in your next annual report (Form 10-K or 20-F) you discuss any material cybersecurity incidents and how you responded, as part of your risk management and governance disclosures[16]. Make sure to capture a summary of this incident for that purpose. Board reports should also be updated – the directors will likely get a full briefing on what happened and how management handled it, so having a clear timeline and documentation (which your data room audit logs and files can provide) is helpful. Additionally, consider if this breach triggers any duty to report to other regulators (privacy regulators, state AGs, etc.) or to law enforcement – those processes might extend beyond the 4-day window but should be on your checklist.
- Learn and adapt: Conduct a post-incident review focusing on the timeline. How well did your team follow the playbook? Did you hit the 4-day deadline comfortably or was it a fire drill? Identify bottlenecks and update the incident response plan (and this playbook) accordingly. This is where having everything in the data room pays dividends – you can literally audit the timestamps to see how long each step took and where delays happened. Use this intel to train and drill the team so that next time (we hope there isn’t a next time, but realistically breaches are ongoing), the 96-hour playbook execution becomes smoother. The ultimate goal is to make this rapid disclosure process muscle memory instead of madness – a routine that, while high-pressure, can be carried out with discipline.
Why a Secure Virtual Data Room is the Backbone of the 4-Day Playbook

You’ve probably noticed a common thread in the playbook: using a secure virtual data room to orchestrate the response. In a high-stakes, time-compressed situation like a breach disclosure (especially during M&A), a data room or similar secure collaboration platform is not just a convenience – it’s mission-critical. Here’s why:
- Centralized, auditable coordination: The data room serves as the single repository for all documents, communications, and decisions during the incident. This means everyone is working off the same up-to-date information, which reduces confusion and version control nightmares.
- Equally important, the platform’s audit logs create an automatic timeline of events – you can show regulators, auditors, or your board exactly when materiality was determined, when drafts were created, who had access, and when the filing was made. These logs help demonstrate that you met the “without unreasonable delay” requirement in making decisions and acted in good faith[3]. If later challenged, you have evidence to back up your actions and timing.
- Leak prevention and access control: By leveraging features like dynamic watermarking, access expiration, and DRM, you massively reduce the risk of premature or unauthorized disclosure of the incident before you’re ready. Every person knows their name is on what they view or download, discouraging leaks. And if something does leak or a device is lost, you can revoke access to the files in question. This kind of rigorous control is nearly impossible to achieve if you rely on email and generic cloud drives during a crisis. The data room essentially puts a protective wrapper around all sensitive documents and discussions, so you can focus on response steps without worrying that the information will escape into the wild.
- Efficient Q&A and stakeholder management: A good VDR platform will have a Q&A or messaging module (for example, CapLinked’s EZ Q&A feature) that allows outsiders to ask questions in a structured way. Using this for breach response means all stakeholder queries (bidders, partners, etc.) flow through one channel and can be triaged to the right subject-matter experts. Nothing gets lost in an email inbox, and all answers are logged. This not only saves time (you avoid answering the same question 5 times in separate calls) but also ensures consistency – everyone gets the same facts. In an investigation aftermath, you can produce the Q&A log to show exactly what was communicated to whom and when, underscoring that you were truthful and even-handed.
- Speed with security: Having your incident playbook tasks executed in a single secure workspace means you don’t waste time juggling tools. The legal team, IT team, execs, and outside parties can collaborate concurrently, which is crucial in a 96-hour window. At the same time, the security features (SSO, IP restrictions, user permissions) mean you can move quickly without sacrificing confidentiality. It’s a balance of agility and control.
- Traceability for post-mortem and legal defense: Let’s face it, a major cyber incident can lead to lawsuits or regulatory inquiries about how the company handled it. By using a data room, you create a forensic record of your incident response. If someone claims “the company dragged its feet” or “selectively disclosed information,” you can counter with logs and document histories. It’s an insurance policy for your process. Plus, internally, it helps identify what went right or wrong in the response for future improvement.
In summary, a disciplined use of a data room is what makes this 4-day breach response playbook feasible. It’s the hub that keeps everyone and everything on track when the clock is ticking loudly.
From Chaos to Routine: Making the 4-Day Rule Work in Practice
The new SEC 4-day breach disclosure rule is stringent, but with the right approach it can be managed confidently. The path to compliance can be summarized in a few fundamental steps: determine materiality quickly, disclose promptly with focused information, and keep all stakeholders informed in a controlled manner. By following the phased playbook above, a company can turn what might be a panicked scramble into a methodical process.
Don’t rely on luck or grace periods. Assume no one will grant you extra time, and that any incident could happen at the worst possible moment (like mid-M&A deal). By preparing in advance – setting up a response team, templates, and a secure collaboration environment – you can execute under pressure as a matter of routine. The first few times will be intense, but repetition builds muscle memory. Conduct tabletop exercises simulating this 4-day sprint to iron out kinks before a real incident hits.
Finally, while we’ve emphasized process and technology, success also hinges on people. Empower your breach response team to make decisions and trust each other. When they know the playbook and have the tools to enforce it (such as a platform with file protections, Q&A, audit logging, etc.), they can focus on what needs to be done rather than how to do it in a rush.
CapLinked’s Role (Agnostic View): As an example, CapLinked’s virtual data room platform is built with these exact scenarios in mind – it offers DRM file protection (through FileProtect), robust user access controls, secure Q&A, and detailed activity reports to support a fast yet secure incident workflow. That said, regardless of which solution you use, the principles remain the same. Use a secure, centralized workspace, enforce strict access discipline, and document everything. This turns a potentially chaotic breach response into a repeatable, defensible process.
In the end, adhering to the 4-day rule is about doing the basics right under time constraints: decide, disclose, and adapt – all while keeping sensitive information on a tight leash. With a solid playbook and the right infrastructure, a 96-hour disclosure sprint can be executed with precision, protecting your investors through timely transparency and protecting your company through prudent control. What could be a nightmare scenario instead becomes a tough but manageable exercise in good governance and crisis management. And that is how you turn compliance from chaos into just another part of doing business in the cyber age.
Sources:
- SEC Form 8-K, Item 1.05 “Material Cybersecurity Incidents” (effective Dec 2023)[17][4][3]
- SEC Release Nos. 33-11216; 34-96299 (July 26, 2023), “Cybersecurity Risk Management, Strategy, Governance, and Incident Disclosure” (adopting release for the 4-day disclosure rule)[18][19]
- Quarles & Brady LLP – SEC Rules Impose New Four-Day Reporting Requirements for Cybersecurity Incidents[1][7]
- WilmerHale – SEC Staff Clarifies Form 8-K Item 1.05 for Cybersecurity Incidents (May 22, 2024)[5][6]
- Baker Donelson – New SEC Rules: Report Material Cyber Incidents Within Four Business Days[20][13]
- Zscaler – Navigating the New SEC Cybersecurity Regulations in M&A Transactions[21][14]
[1] [2] [7] [8] [16] [18] [19] SEC Rules Impose New Four-Day Reporting Requirements for Cybersecurity Incidents: Quarles Law Firm, Attorneys, Lawyers
[3] [4] [9] [10] [11] [12] [17] Form 8-K
https://www.sec.gov/files/form8-k.pdf
[5] [6] SEC Staff Clarifies Form 8-K Item 1.05 is for Cybersecurity Incidents that are Determined to be Material
[13] [20] New SEC Rules: Public Companies Must Report Material Cybersecurity Incidents Within Four Business Days | Baker Donelson
[14] [15] [21] Navigating the new SEC cybersecurity regulations in M&A